Are you 100% safe? Do you have endpoint protection in place, firewalls defending the perimeter, and phishing filters on incoming email. Do leveraged tools to check for anomalies in your network traffic, rolled out an SSO solution, and implemented processes to securely connect to the network remotely sound familiar to you?
All of the above make it difficult and hard for attackers to attack and damage your organization. It may be that your weakest point is not within your own organization, but within one of your suppliers. You trust their products and services, relying on them to conduct business. Unfortunately, if their security posture isn’t as mature as yours, attackers can exploit that trust and use it in attacks.
This is what a supply chain attack is. In these attacks, bad actors compromise a secondary organization that supplies software or services to a primary, target organization. Their goal is to compromise the primary target when they use the software or service of the secondary target.
How the attack works
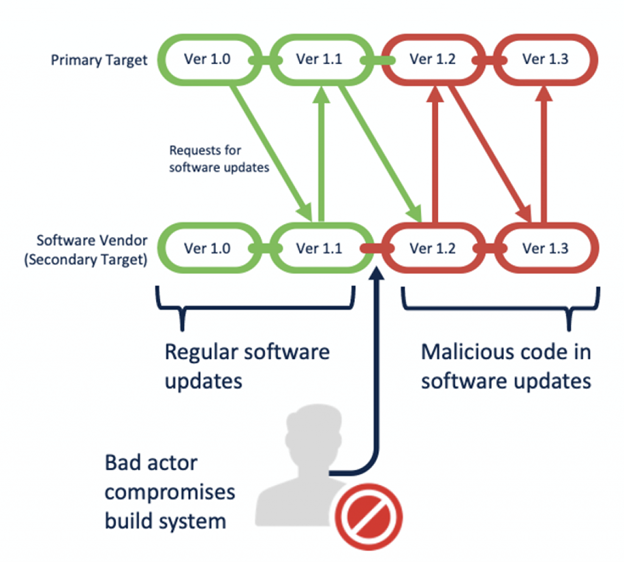
Although there are several ways to attack a supply chain, there is a general pattern seen in many attacks. First, the bad actors gather what information they can find about the external products and services used by the primary target. The attackers assess the suppliers of those products and services and then choose a secondary target, based on what they discover. This secondary target now becomes the fulcrum of the attack.
Next, the bad actors attempt to compromise the secondary target. The ways they go about doing so will vary, often choosing the path of least resistance. They could try anything from spear phishing to exploiting vulnerabilities at the network edge. The choice will largely depend on the secondary target itself—where the attackers perform reconnaissance to determine the approach most likely to lead to a successful breach.
Once in, the attackers move laterally, their objective often being to compromise the secondary target’s software build system, where the source code for their software is stored, updated, and compiled. One of the easiest ways to achieve this is by compromising a developer’s machine, or their credentials, gaining the required access. With access to the build system, the attackers can surreptitiously insert malicious code, like a backdoor or RAT, into the software in question. The secondary target, unaware of the presence of malicious code, compiles the latest updates, signs the binary, and then releases it.
At this point the attackers wait for the primary organization to download and install the compromised update. Once this occurs, the malware phones home and attackers are in, now having access into the primary organization they intended to compromise.
Notable examples
There are several supply chain attacks that have made headlines. One of the most notable happened last year, when bad actors compromised software updates to SolarWind’s Orion IT management software. The attackers managed to stay hidden for months, during which multiple US government agencies and corporations were compromised.
In 2017, the wiper malware NotPetya is believed to have begun its spread by leveraging the update system of the Ukrainian tax software, M.E.Doc. This attack led to widespread compromises in the Ukraine, and across the globe, resulting in billions of dollars in damage.
Later that same year, bad actors managed to insert a backdoor into the popular PC maintenance tool, CCleaner. The compromised versions were downloaded over 2.27 million times .
The defense dilemma
The toughest part about supply chain attacks is that the vector used to compromise the primary target is hidden within legitimate software. This makes supply chain attacks incredibly difficult to protect against, presenting a number of challenges.
First, supply chain attacks compromise software that your organization already uses and trusts. Inserting bad code into trusted software makes it notoriously difficult to identify the malicious activity.
Patching is a vital part of any security strategy. It is particularly ironic that in the case of so many supply chain attacks, the malicious functionality is distributed by abuse of the patching and update mechanism by bad actors.
This presents a catch-22, whereby an errant patch could result in a supply chain compromise, but not patching could lead to other security risks, such as exploitation via unpatched vulnerabilities.
Caught in the act
A supply chain attack is difficult to recognize and the attacker will still have to traverse a network, moving laterally to get to their goal. Also, if stealing information is their aim, they will still need to exfiltrate said data. And through it all, they will need to perform command and control activity to instruct the malicious software to do what they need it to do.
These are all great touchpoints to detect, block, and remediate such an attack. For instance, keep an eye out for any of the following:
- Look for unauthorized changes or unusual software additions on endpoints. Attackers often modify endpoints, or install software like webshells, to further their attacks.
- Monitor for unexpected use of credentials. When machines are compromised, credentials are often scraped and used to log into other devices on the network.
- Pay particular attention to key systems, such as active directory servers or other domain controllers.
Focusing on response
With prevention being difficult, if not an unattainable goal, response becomes a more viable approach to defend against supply chain attacks. One way to do this is with extended detection and response (XDR) solutions. Such solutions give visibility across networks, endpoints, and applications to analyze, hunt, and remediate attacks.
What should provide you with such a solution? First of all, achieving business intelligence by aggregating threat information, in-depth search to see where a particular activity started, monitoring the situation over the network to get a broader picture, and then the ability to take corrective action directly from the interface, blocking suspicious items on the spot.
Solutions that provide an integrated security architecture, visibility of all components, and learning from the data it collects - greatly simplifies threat and response investigations for the organization. By this we mean the security of applications, processes, systems; recognizing suspicious and unexpected online activity, as well as preventing data retrieval, rule violations and other sophisticated techniques used by attackers. You should always know who, what, where and how connected and how endpoints and devices are connected. Detecting anomalies in the behavior of applications can help identify attacks.
This may be too much information, but staying cyber secure these days is complex and requires your full readiness.